Tracking Down Repeat Failed Login Attempts to Domain Controller
One of our clients kept getting repeat failed login attempts on their domain controller. Usually this is an issue with a port being open on the firewall and brute-force attacks being run to guess the password, but ports were closed on the firewall and it didn’t look like a dictionary attack. Instead, it looked like something was running every 2 minutes, attempting to use the guest account.
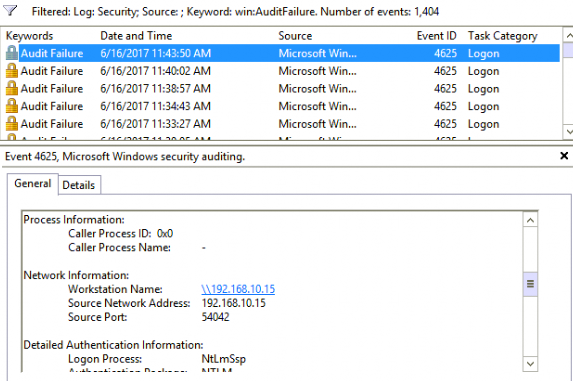
The first thing we did was filter the security log in the Event Log by keyword: Audit Failure. This allowed us to see how often all the audit failures were. Conveniently, they were about every 2 minutes. (Convenient because we have a few chances to catch the culprit!) We could see that the source port was changing every time, adding complexity to the issue.
The audit log provided the IP address of the workstation as well as the username that was trying to authenticate.
We were interested in what the hostname was of the workstation, so we ran ping -a 192.168.10.15 and got the hostname. Now we know the PCs name and the account that is failing authentication. We have found the offender!
We used our remote support tools to connect to the PC, then wrote a script to monitor the port traffic. This script is just an infinite loop, dumping out the output of netstat -ano.
:loop
netstat -ano >> ports.txt
goto loop
We saved this as monitor.bat and ran on the offending machine. Then we went to the domain controller and watched for the event to happen. Once we had the Source Port from the new event, we went back to the offending machine, pressed Ctrl+C, terminated the script, and opened the ports.txt file. We were able to search the text file for the Source Port and get the Process ID of the offending process.
With this information, we were able to open a command prompt and find the offending process.
tasklist /v | findstr /i "54042"
From there we were able to make changes to the process to allow it to authenticate correctly, if necessary, or remove the process if not necessary.